In the digital age, IP (Internet Protocol) addresses have become the fundamental building blocks of online communication and connectivity. These numerical identifiers are assigned to each device connected to a computer network that utilizes the Internet Protocol. IP addresses serve as the digital addresses that enable devices to find and communicate with one another across the vast expanse of the internet.
There are two primary versions of IP addresses in use today: IPv4 (Internet Protocol version 4) and IPv6 (Internet Protocol version 6). IPv4 addresses are composed of four sets of numbers, each ranging from 0 to 255, separated by periods (e.g., 192.168.1.1). As the original and most widely adopted IP address standard, IPv4 has faced challenges due to the limited number of available addresses. This led to the development of IPv6, which uses a longer, hexadecimal-based format consisting of eight groups of four hexadecimal digits separated by colons (e.g., 2001:0db8:85a3:0000:0000:8a2e:0370:7334).
The Threat of IP Address Fraud
IP address fraud, also known as IP address spoofing, refers to the malicious practice of manipulating or falsifying the source IP address in network communications. Attackers engage in this deceptive technique for various reasons, including:
- Hiding True Identity: By masking their true IP address, attackers can conceal their identity and the origin of their activities, making it more challenging to trace and attribute their actions.
- Bypassing Security Measures: Spoofed IP addresses can circumvent access controls, firewalls, and other security measures that rely on IP address-based authentication or filtering.
- Launching Cyber Attacks: Attackers may leverage spoofed IP addresses to carry out various types of cyber attacks, such as distributed denial-of-service (DDoS) attacks, network intrusions, or the dissemination of malware.
- Impersonating Legitimate Entities: Fraudsters may use spoofed IP addresses to impersonate trusted organizations, individuals, or services, enabling them to conduct phishing campaigns, steal sensitive data, or perpetrate financial fraud.
The consequences of IP address fraud can be severe, ranging from financial losses and reputational damage to regulatory compliance issues and broader cybersecurity risks. Organizations must take proactive steps to detect and mitigate these threats to safeguard their online presence and protect their assets.
Techniques for IP Address Fraud Check
To combat the growing threat of IP address fraud, organizations can employ a range of techniques and strategies. Here are some of the key approaches:
Geolocation Analysis
One of the most common methods for IP address fraud checks is geolocation analysis. This technique involves leveraging databases or services that map IP addresses to their corresponding geographic locations. By comparing the reported location of an IP address with the expected or known location of the user or device, organizations can identify potential discrepancies that may indicate fraudulent activity.
Geolocation analysis can be particularly useful in scenarios where an IP address is associated with a location that is significantly different from the user’s usual location or the expected location based on other contextual information. This can help detect attempts to conceal the true origin of an IP address or impersonate a user from a different geographic region.
Reputation-based Checks
Another approach to IP address fraud checks is to perform reputation-based checks. These checks involve consulting databases or services that maintain lists of IP addresses known to be associated with malicious or fraudulent activities, such as botnet command and control servers, phishing sites, or spam sources.
By cross-checking an IP address against these reputation databases, organizations can assess the trustworthiness and potential risk associated with a specific IP address. This information can then be used to make informed decisions about the legitimacy of the IP address and the level of trust that should be placed in it.
Reputation-based checks can be particularly effective in identifying known threats and preventing the exploitation of IP addresses that have been previously associated with malicious behavior.
Behavioral Analysis
Behavioral analysis is a more advanced technique for IP address fraud checks. This approach involves monitoring and analyzing the patterns of activity and behavior associated with an IP address over time. By identifying anomalies or unusual patterns, such as sudden changes in location, device type, or online activity, organizations can detect potentially fraudulent behavior and take appropriate action.
Behavioral analysis can be particularly useful in detecting attempts to impersonate legitimate users or entities, as well as identifying coordinated attacks or campaigns that involve the use of multiple IP addresses. By establishing a baseline of normal behavior and continuously monitoring for deviations, organizations can enhance their ability to identify and respond to IP address fraud.
Multi-factor Authentication
To further strengthen IP address fraud check, organizations may implement multi-factor authentication (MFA) mechanisms. MFA requires users to provide additional verification, such as a one-time code, biometric data, or a physical security key, in addition to their IP address.
This layered approach to authentication can make it more difficult for attackers to impersonate legitimate users and gain unauthorized access, even if they have managed to spoof an IP address. By introducing additional verification factors, MFA helps ensure that the user’s identity and access privileges are properly validated, reducing the risk of successful IP address fraud.
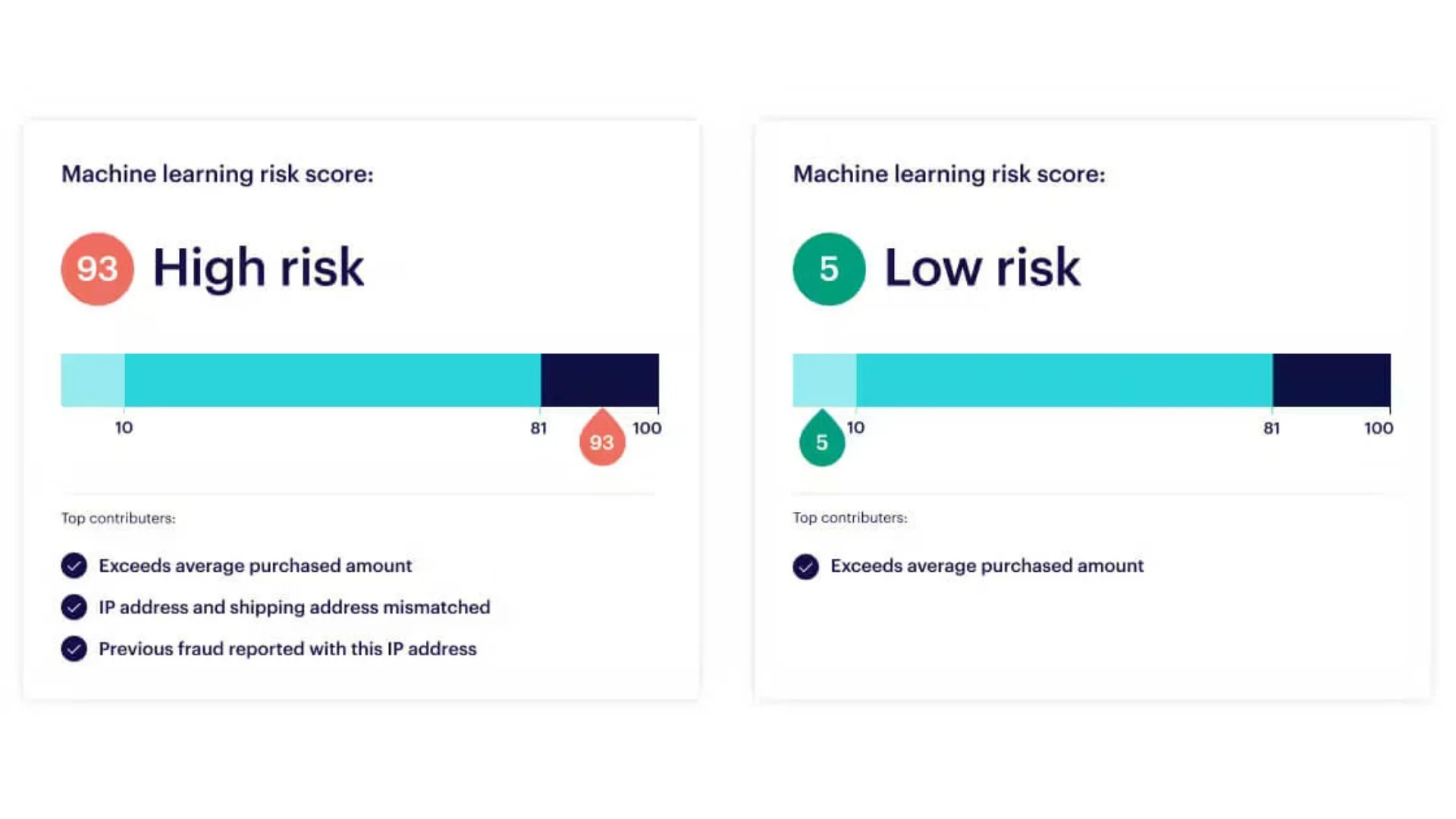
Anomaly Detection and Machine Learning
Advanced techniques for IP address fraud check may involve the use of anomaly detection and machine learning algorithms. These approaches analyze large datasets of IP address-related information, such as network traffic patterns, user behavior, and historical data, to identify unusual or suspicious activity that could indicate fraud.
By continuously learning and adapting to new threats, these techniques can help organizations stay ahead of evolving fraud tactics. Anomaly detection algorithms can identify patterns, trends, and deviations that may signal IP address fraud, while machine learning models can be trained to recognize and classify known and emerging fraud patterns.
The integration of these advanced analytics capabilities can provide organizations with a more comprehensive and adaptive approach to IP address fraud check, enhancing their ability to detect and respond to sophisticated attacks.
The Importance of IP Address Fraud Check
The importance of effective IP address fraud check cannot be overstated, as it directly impacts an organization’s ability to safeguard its systems, networks, and assets. Here are some of the key reasons why IP address fraud check is critical:
Financial Losses
Fraudulent activities enabled by IP address spoofing, such as unauthorized access to accounts or systems, can lead to significant financial losses through theft, fraud, or ransomware attacks. These losses can have a substantial impact on an organization’s bottom line and threaten its financial stability.
Reputational Damage
If an organization’s systems or services are compromised due to IP address fraud, it can result in significant reputational damage. This erosion of trust and confidence among customers, partners, and the general public can be challenging to recover from and can have long-lasting consequences for the organization’s brand and market standing.
Regulatory Compliance Issues
Many industries and sectors are subject to strict regulations and standards, such as the General Data Protection Regulation (GDPR) or the Payment Card Industry Data Security Standard (PCI DSS). Failure to implement effective IP address fraud check measures can lead to compliance violations and associated penalties, further compounding the impact on the organization.
Cybersecurity Risks
IP address fraud can be a gateway for various types of cyber attacks, such as distributed denial-of-service (DDoS) attacks, network intrusions, or the spread of malware. Effective IP address fraud check helps mitigate these risks and protect the integrity of an organization’s systems and networks, reducing the likelihood of successful attacks and the associated consequences.
Privacy Concerns
IP address fraud can also compromise the privacy of individuals, as their personal information or online activities may be exposed or misused without their knowledge or consent. Addressing IP address fraud is crucial for maintaining the privacy and security of sensitive data.
By implementing comprehensive IP address fraud check measures, organizations can safeguard their financial assets, protect their reputation, ensure regulatory compliance, enhance their cybersecurity posture, and uphold the privacy and trust of their stakeholders.
Best Practices for IP Address Fraud Check
To effectively combat IP address fraud, organizations should consider implementing the following best practices:
- Maintain a Comprehensive IP Address Inventory: Organizations should maintain a detailed inventory of all IP addresses associated with their systems, devices, and services. This helps establish a baseline for identifying and verifying legitimate IP addresses, enabling more effective detection of anomalies or unauthorized access attempts.
- Utilize Geolocation Services: Leveraging geolocation services can provide valuable insights into the geographic location of IP addresses, enabling organizations to detect and investigate any discrepancies between the reported location and the expected or known location of the user or device.
- Integrate Reputation-based Checks: Regularly checking IP addresses against reputable databases or services that track known malicious or fraudulent IP addresses can help identify and mitigate potential threats. This includes maintaining awareness of evolving threat landscapes and updating the organization’s reputation-based checks accordingly.