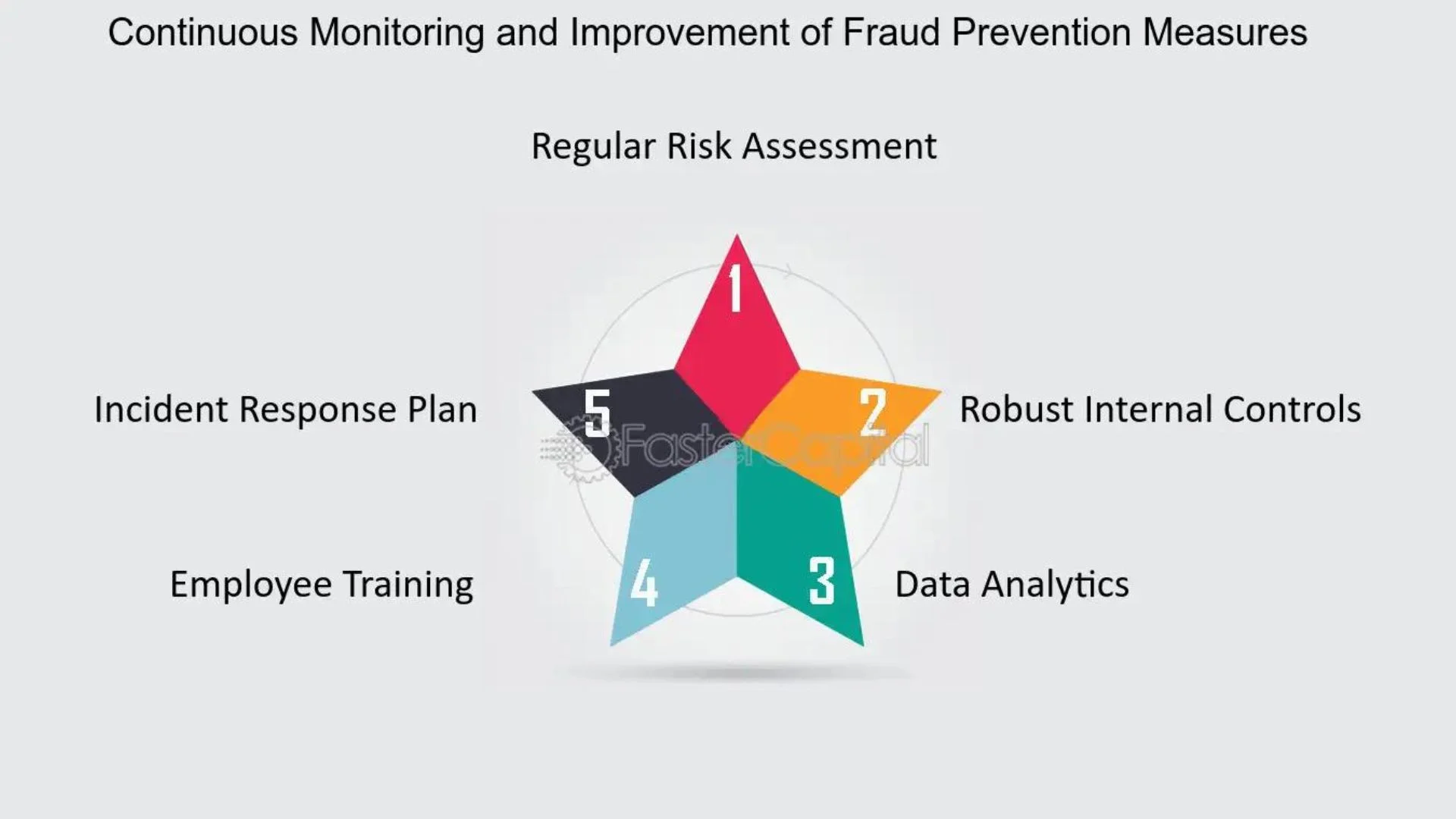
The advent of 4G (fourth-generation) cellular technology has ushered in a new era of lightning-fast mobile connectivity, revolutionizing the way we communicate, access information, and conduct business. With download speeds up to 100 times faster than previous 3G networks, 4G has enabled a proliferation of data-intensive applications, real-time video streaming, and seamless mobile experiences.Extension 4G ) Fraud Risk
However, this technological advancement has also introduced new avenues for fraud and cybercriminal activity. As 4G networks become more widespread, fraudsters have adapted their tactics to exploit the vulnerabilities inherent in this evolving landscape. Understanding the unique fraud risks associated with 4G is crucial for organizations and individuals to safeguard against the growing threat.
Anatomy of 4G Fraud: Emerging Threats and Vulnerabilities
The transition from 3G to 4G networks has brought about a shift in the fraud landscape, with new and more sophisticated attack vectors emerging. Here are some of the key fraud risks associated with 4G technology:
Subscriber Identity Theft and SIM Swapping
One of the primary fraud risks in the 4G era is the theft of subscriber identities and the exploitation of the SIM (Subscriber Identity Module) card. Fraudsters have developed techniques to hijack subscriber accounts, often through social engineering or malware, and then use the compromised credentials to gain unauthorized access to 4G networks and services.
SIM swapping, a particularly prevalent form of identity theft, involves tricking a mobile carrier into transferring a victim’s phone number to a SIM card controlled by the attacker. This allows the fraudster to intercept the victim’s calls, text messages, and two-factor authentication codes, enabling them to access sensitive accounts and financial information.
Signaling System Vulnerabilities
The 4G network architecture relies on a complex signaling system, known as the IP Multimedia Subsystem (IMS), to manage various communication protocols and services. Unfortunately, this signaling system has inherent vulnerabilities that can be exploited by cybercriminals.
Fraudsters may target the signaling system to launch denial-of-service (DoS) attacks, disrupt network operations, or intercept and manipulate sensitive data. These attacks can lead to service disruptions, financial losses, and the compromise of user privacy and security.
Rogue Base Stations and IMSI Catchers
Another emerging threat in the 4G landscape is the use of rogue base stations and IMSI (International Mobile Subscriber Identity) catchers. These devices mimic legitimate cellular towers, tricking mobile devices into connecting to the fraudulent network, where the attacker can then intercept communications, track user locations, and even execute man-in-the-middle attacks.
These malicious base stations can be set up in public areas, exploiting the seamless handover between 4G cells to lure unsuspecting users and gain unauthorized access to their devices and data.
Exploitation of IoT Vulnerabilities
The proliferation of Internet of Things (IoT) devices, which often rely on 4G connectivity, has introduced new avenues for fraud. Cybercriminals can target poorly secured IoT devices, such as smart home appliances, wearables, or industrial equipment, to gain access to sensitive information, disrupt operations, or even launch large-scale attacks.
Fraudsters may also exploit vulnerabilities in the communication protocols and firmware of IoT devices to hijack them and use them as part of a botnet for further malicious activities, such as distributed denial-of-service (DDoS) attacks.
Combating 4G Fraud: Strategies and Best Practices
As the 4G fraud landscape continues to evolve, it is crucial for organizations and individuals to adopt comprehensive strategies to mitigate these risks. Here are some key measures that can help enhance 4G security and protect against fraud:
Robust Identity and Access Management
Implementing robust identity and access management (IAM) solutions is crucial in the 4G era. This includes the use of strong authentication methods, such as multi-factor authentication (MFA), biometric identification, and behavioral analytics, to verify the identity of users and devices accessing 4G networks and services.
Organizations should also closely monitor user activities and behavior patterns to detect and respond to suspicious activities, such as unauthorized access attempts or unusual transaction patterns.
Secure Signaling System Architecture
To address the vulnerabilities in the 4G signaling system, network operators and service providers must prioritize the security of their IMS architecture. This includes implementing advanced security protocols, such as IPsec (Internet Protocol Security) and DTLS (Datagram Transport Layer Security), to encrypt and secure signaling traffic.Extension 4G ) Fraud Risk
Additionally, the adoption of secure protocol gateways, firewalls, and intrusion detection and prevention systems can help mitigate the risk of signaling-based attacks.
Rogue Base Station Detection and Mitigation
Combating the threat of rogue base stations and IMSI catchers requires a multi-pronged approach. Network operators should deploy advanced detection mechanisms, such as radio frequency (RF) fingerprinting and network traffic analysis, to identify and locate malicious base stations.
Additionally, end-users should be educated on the risks of public Wi-Fi networks and the importance of verifying the legitimacy of cellular connections before sharing sensitive information or conducting transactions.Extension 4G ) Fraud Risk
IoT Security Enhancements
Addressing the fraud risks associated with IoT devices in the 4G ecosystem requires a comprehensive approach, including:
- Implementing strong device authentication and access control measures to prevent unauthorized access.
- Regularly updating IoT device firmware and software to address known vulnerabilities.
- Leveraging security-by-design principles in the development of IoT products and services.
- Fostering collaboration between IoT manufacturers, network providers, and security researchers to identify and address emerging threats.
Regulatory Compliance and Industry Collaboration
Effective mitigation of 4G fraud risks also requires close collaboration between industry stakeholders, regulatory bodies, and law enforcement agencies. Network operators, service providers, and device manufacturers should work together to develop and adhere to industry-wide security standards and best practices.Extension 4G ) Fraud Risk
Additionally, regulatory frameworks and guidelines, such as the 3GPP (3rd Generation Partnership Project) security specifications and the GSMA (GSM Association) security recommendations, should be closely followed to ensure compliance and enhance the overall security of 4G networks and services.
Conclusion
The transition to 4G technology has unlocked new possibilities for mobile connectivity and innovation, but it has also opened the door to a evolving landscape of fraud risks. Subscriber identity theft, signaling system vulnerabilities, rogue base stations, and IoT security challenges are just a few of the threats that organizations and individuals must navigate in the 4G era.Extension 4G ) Fraud Risk
To stay ahead of these emerging fraud risks, a holistic and proactive approach is necessary. By implementing robust identity and access management solutions, securing the signaling system architecture, deploying rogue base station detection mechanisms, and enhancing IoT security, stakeholders can significantly reduce the risk of 4G-related fraud and safeguard the integrity of the 4G ecosystem.
Continuous collaboration between industry players, regulatory bodies, and law enforcement agencies is also crucial to stay informed about the latest fraud trends, share intelligence, and develop effective countermeasures. By staying vigilant and adopting a comprehensive security strategy, organizations and individuals can embrace the benefits of 4G technology while mitigating the risks of fraud.
As the 4G network continues to evolve and new generations of cellular technology emerge, the fraud landscape will undoubtedly continue to change. However, by proactively addressing the unique challenges posed by 4G, we can build a more secure and resilient mobile ecosystem that empowers innovation, protects user privacy, and safeguards against the ever-evolving threat of fraud.